Numerical Validation of UAV‑CRN Optimization: Improved Rates Under Energy and PLoS Constraints
Table of Links
Abstract and I. Introduction
II. System Model
III. Problem Formulation
IV. Proposed Algorithm for Problem P0
V. Numerical Results
VI. Conclusion
APPENDIX A: PROOF OF LEMMA 1 and References
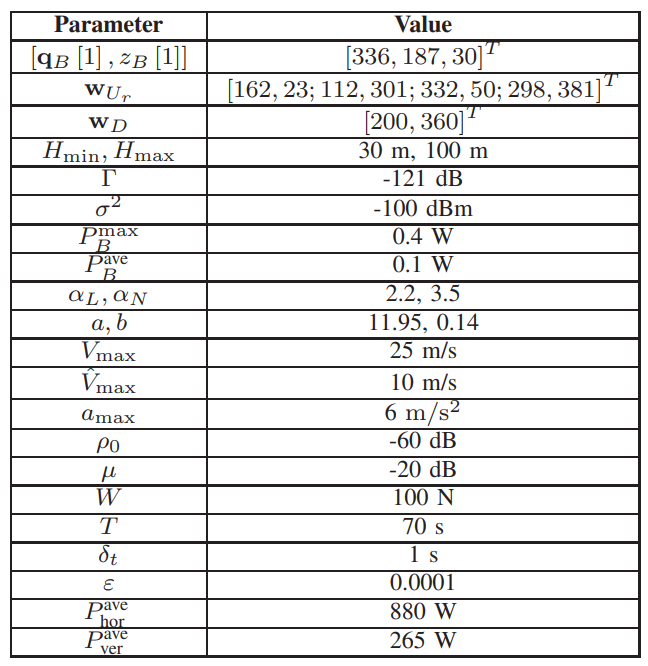
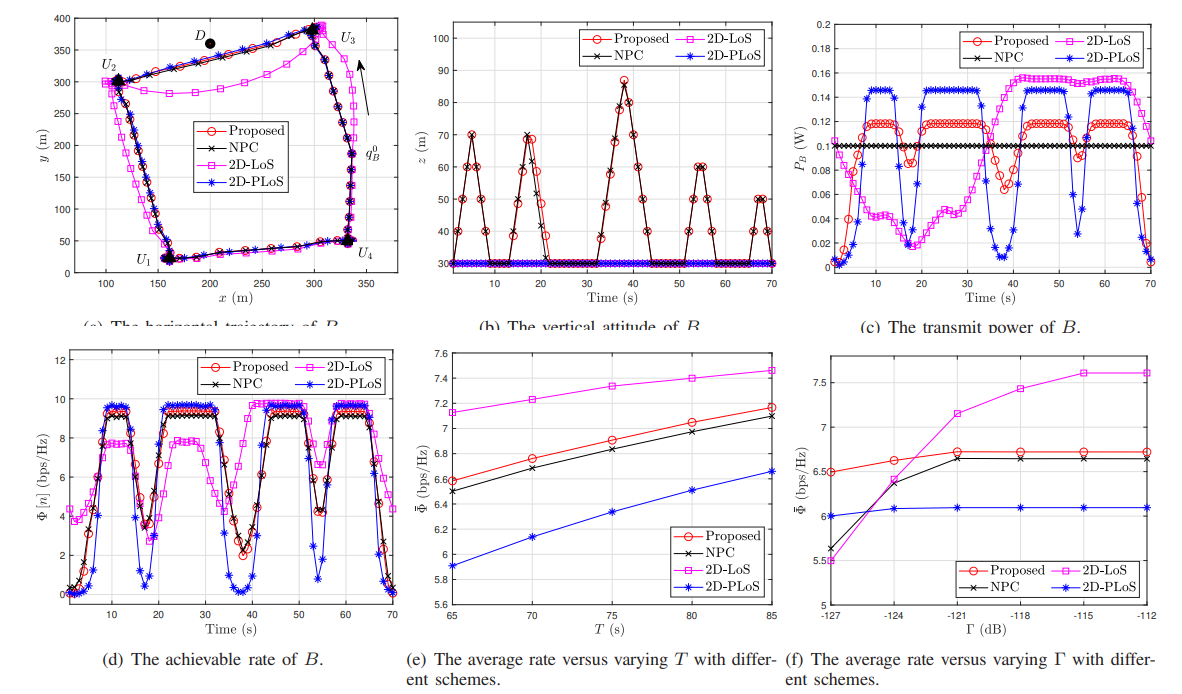
V. NUMERICAL RESULTS
In this section, extensive simulations are conducted to validate the effectiveness and the convergence of the proposed algorithm. To illustrate the advantages of the proposed algorithm, the following three benchmark schemes are compared.
\
-
Benchmark I: B transmit signals with the average power and both 3D trajectory of B and user scheduling are jointly optimized based on the PLoS model, which is denoted by ‘NPC’.
\
-
Benchmark II: The 2D trajectory of B, the transmission power of B, and user scheduling are jointly optimized based on the LoS model, which is denoted by ‘2D-LoS’.
\
-
Benchmark III: B works with fixed vertical trajectory and its horizontal and transmission power of B, and user scheduling are jointly optimized based on the PLoS model, which is denoted by ‘2D-PLoS’.
\ 
\ 
\ 
\ 
\ Figs. 4(a) and 4(b) provide the 3D trajectory of B with the different schemes and in the scenarios with different propulsion power limitations, respectively. From Fig. 4(a), it can be observed that compared with the scenarios with the 2D-PLoS scheme, B in the 2D-LoS scheme must keep away from D to meet IT constraints. This requirement for B to keep away from D in the 2D-LoS scheme is due to the exaggerated probability of LoS for the A2G link. The results in Fig. 4(b) show that different propulsion power limitation results in different vertical trajectories
\ 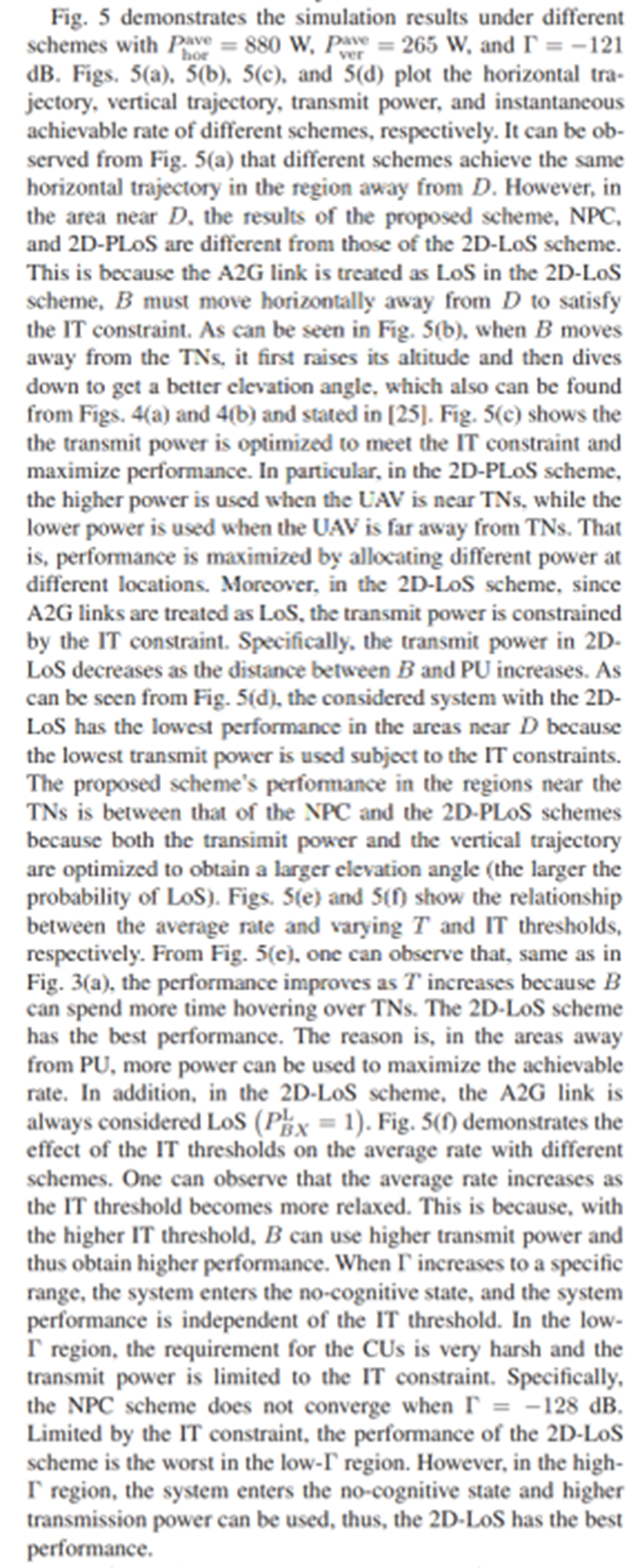
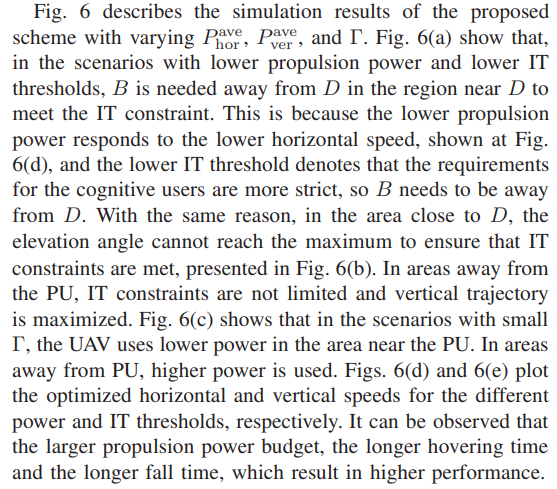
\ 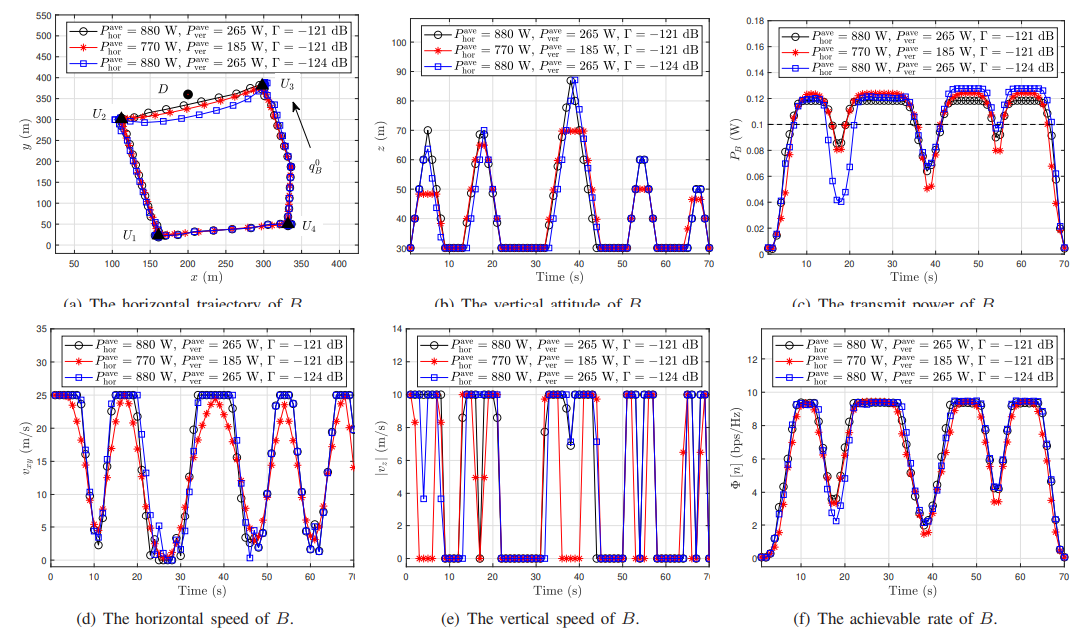
\ 
\
VI. CONCLUSION
This work investigated the achievable rate of the underlay IoT system with an energy-constrained UAV under PLoS channels. The achievable rate of the considered systems was maximized by jointly considering the UAV’s 3D trajectory, transmission power, and user scheduling, which is a nonlinear mixed-integer non-convex problem. The lower bound of the average achievable rate was utilized and the original nonconvex problem was transformed into several solvable convex subproblems by using BCD and SCA techniques, and an efficient iterative algorithm was proposed. The numerical results not only verified the convergence and effectiveness of the algorithm but also illustrated the impact of propulsion power and interference thresholds on the average achievable rate
\
APPENDIX A
PROOF OF LEMMA 1
\ 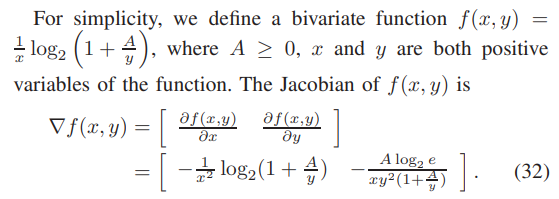
\ \ From the above Jacobian matrix, we can obtain the Hessian matrix of f(x, y) as
\ \ 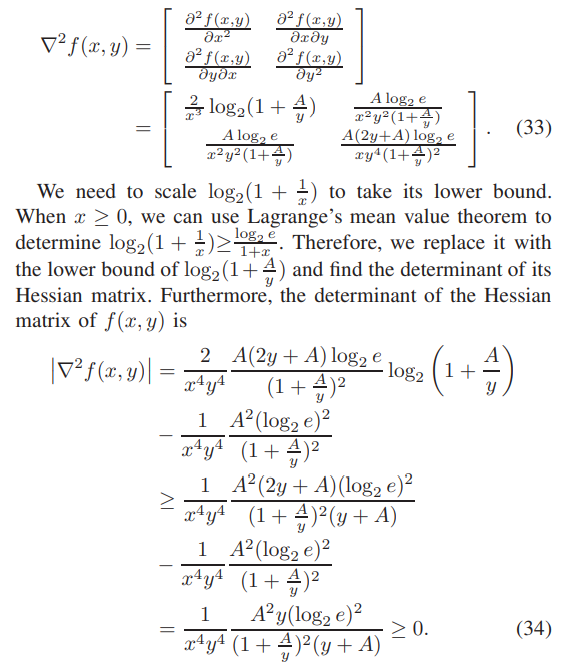
\ \ According to (33) and (34), for any given A ≥ 0, We can determine that the determinant of the cofactor matrix of the Hessian matrix of function f(x, y) is greater than or equal to 0. Therefore, the Hessian matrix of f(x, y) is a semi-positive definite matrix, so f(x, y) is a convex function.
\
REFERENCES
[1] Q. Wu, J. Xu, Y. Zeng, D. W. K. Ng, N. Al-Dhahir, R. Schober, and A. L. Swindlehurst, “A comprehensive overview on 5G-and-beyond networks with UAVs: From communications to sensing and intelligence,” IEEE J. Sel. Areas Commun., vol. 39, no. 10, pp. 2912-2945, Oct. 2021.
\ [2] B. Li, Z. Fei, and Y. Zhang, “UAV communications for 5G and beyond: recent advances and future trends,” IEEE Internet Things J., vol. 6, no. 2, pp. 2241-2263, Apr. 2019.
\ [3] Y. Zeng, Q. Wu, and R. Zhang, “Accessing from the sky: A tutorial on UAV communications for 5G and beyond,” Proc. IEEE, vol. 107, no. 12, pp. 2327-2375, Dec. 2019.
\ [4] Q. Wu, L. Liu, and R. Zhang, “Fundamental trade-offs in communication and trajectory design for UAV-enabled wireless network,” IEEE Wireless Commun., vol. 26, no. 1, pp. 36-44, Feb. 2019.
\ [5] Q. Wu, Y. Zeng, and R. Zhang, “Joint trajectory and communication design for multi-UAV enabled wireless networks,” IEEE Trans. Wireless Commun., vol. 17, no. 3, pp. 2109-2121, Mar. 2018.
\ [6] Z. Li, M. Chen, C. Pan, N. Huang, Z. Yang, and A. Nallanathan, “Joint trajectory and communication design for secure UAV networks,” IEEE Commun. Lett., vol. 23, no. 4, pp. 636-639, Apr. 2019.
\ [7] H. Fu, Z. Sheng, A. A. Nasir, A. H. Muqaibel, and L. Hanzo, “Securing the UAV-aided non-orthogonal downlink in the face of colluding eavesdroppers,” IEEE Trans. Veh. Technol., vol. 71, no. 6, pp. 6837-6842, Jun. 2022.
\ [8] M. Cui, G. Zhang, Q. Wu, and D. W. K. Ng, “Robust trajectory and transmit power design for secure UAV communications,” IEEE Trans. Veh. Technol., vol. 67, no. 9, pp. 9042-9046, Sep. 2018.
\ [9] Y. Zeng and R. Zhang, “Energy-efficient UAV communication with trajectory optimization,” IEEE Trans. Wireless Commun., vol. 16, no. 6, pp. 3747-3760, Jun. 2017.
\ [10] S. Eom, H. Lee, J. Park, and I. Lee, “UAV-aided wireless communication designs with propulsion energy limitations,” IEEE Trans. Veh. Technol., vol. 69, no. 1, pp. 651-662, Jan. 2020.
\ [11] Y. Wu, W. Yang, X. Guan, and Q. Wu, “Energy-efficient trajectory design for UAV-enabled communication under malicious jamming,” IEEE Wireless Commun. Lett., vol. 10, no. 2, pp. 206-210, Feb. 2021.
\ [12] J. Zhang, Y. Zeng, and R. Zhang, “Receding horizon optimization for energy-efficient UAV communication,” IEEE Wireless Commun. Lett., vol. 9, no. 4, pp. 490-494, Apr. 2020.
\ [13] A. Bejaoui, K.-H. Park, and M.-S. Alouini, “A QoS-oriented trajectory optimization in swarming unmanned-aerial-vehicles communications,” IEEE Wireless Commun. Lett., vol. 9, no. 6, pp. 791-794, Jun. 2020.
\ [14] Y. Zeng, J. Xu, and R. Zhang, “Energy minimization for wireless communication with rotary-wing UAV,” IEEE Trans. Wireless Commun., vol. 18, no. 4, pp. 2329-2345, Apr. 2019.
\ [15] C. Zhan and H. Lai, “Energy minimization in internet-of-things system based on rotary-wing UAV,” IEEE Wireless Commun. Lett., vol. 8, no. 5, pp. 1341-1344, Oct. 2019.
\ [16] B. Duo, Q. Wu, X. Yuan, and R. Zhang, “Energy efficiency maximization for full-duplex UAV secrecy communication,” IEEE Trans. Veh. Technol., vol. 69, no. 4, pp. 4590-4595, Apr. 2020.
\ [17] R. Zhang, X. Pang, W. Lu, N. Zhao, Y. Chen, and D. Niyato, “Dual-UAV enabled secure data collection with propulsion limitation,” IEEE Trans. Wireless Commun., vol. 20, no. 11, pp. 7445-7459, Nov. 2021.
\ [18] M. Li, X. Tao, N. Li, H. Wu, and J. Xu, “Secrecy energy efficiency maximization in UAV-enabled wireless sensor networks without eavesdropper’s CSI,” IEEE Internet Things J., vol. 9, no. 5, pp. 3346-3358, Mar. 2022.
\ [19] A. Al-Hourani, S. Kandeepan, and S. Lardner, “Optimal LAP altitude for maximum coverage,” IEEE Wireless Commun. Lett., vol. 3, no. 6, pp. 569-572, Dec. 2014.
\ [20] B. Duo, H. Hu, Y. Li, and X. Yuan, “Joint trajectory and power design in probabilistic LoS channel for UAV-enabled cooperative jamming,” Proc. IEEE International Conference on Communications (ICC 2021), Montreal, QC, Canada, Jun. 2021, pp. 1-6.
\ [21] C. You and R. Zhang, “Hybrid offline-online design for UAV-enabled data harvesting in probabilistic LoS channels,” IEEE Trans. Wireless Commun., vol. 19, no. 6, pp. 3753-3768, Jun. 2020.
\ [22] B. Duo, Q. Wu, X. Yuan, and R. Zhang, “Anti-jamming 3D trajectory design for UAV-enabled wireless sensor networks under probabilistic LoS channel,” IEEE Trans. Veh. Technol., vol. 69, no. 12, pp. 16288-16293, Dec. 2020.
\ [23] Z. Guan, S. Wang, L. Gao, and W. Xu, “Energy-efficient UAV communication with 3D trajectory optimization,” Proc. 2021 7th International Conference on Computer and Communications (ICCC), Chengdu, China, Dec. 2021, pp. 312-317.
\ [24] A. Meng, X. Gao, Y. Zhao, and Z. Yang, “Three-dimensional trajectory optimization for energy-constrained UAV-enabled IoT system in probabilistic LoS channel,” IEEE Internet Things J., vol. 9, no. 2, pp. 1109- 1121, Jan. 2022.
\ \ [25] H. Lei, H. Ran, I. S. Ansari, K.-H. Park, G. Pan, and M.-S. Alouini, “DDPG-based aerial secure data collection,” IEEE Trans. Commun., doi: 10.1109/TCOMM.2024.3379417, 2024.
\ [26] Y. Saleem, M. H. Rehmani, and S. Zeadally, “Integration of cognitive radio technology with unmanned aerial vehicles: Issues, opportunities, and future research challenges,” J. Netw. Comput. Appl., vol. 50, pp. 15- 31, Apr. 2015.
\ [27] H. Lei, H. Yang, K.-H. Park, I. S. Ansari, J. Jiang, and M.-S. Alouini, “Joint trajectory design and user scheduling for secure aerial underlay IoT systems,” IEEE Internet Things J., vol. 10, no. 15, pp. 13637-13648, Aug. 2023.
\ [28] H. Lei, J. Jiang, H. Yang, K.-H. Park, I. S. Ansari, G. Pan, and M.-S. Alouini. “Trajectory and power design for aerial CRNs with colluding eavesdroppers,” arXiv:2310.13931, Oct. 2023, [Online]: https://arxiv.org/abs/2310.13931
\ [29] P. X. Nguyen, V.-D. Nguyen, H. V. Nguyen, and O.-S. Shin, “UAVassisted secure communications in terrestrial cognitive radio networks: Joint power control and 3D trajectory optimization,” IEEE Trans. Veh. Technol., vol. 70, no. 4, pp. 3298-3313, Apr. 2021.
\ [30] Z. Wang, F. Zhou, Y. Wang, and Q. Wu, “Joint 3D trajectory and resource optimization for a UAV relay-assisted cognitive radio network,” China Commun., vol. 18, no. 6, pp. 184-200, Jun. 2021.
\ [31] Y. Huang, W. Mei, J. Xu, L. Qiu, and R. Zhang, “Cognitive UAV communication via joint maneuver and power control,” IEEE Trans. Commun., vol. 67, no. 11, pp. 7872-7888, Nov. 2019.
\ [32] Y. Jiang and J. Zhu, “Three-dimensional trajectory optimization for secure UAV-enabled cognitive communications,” China Commun., vol. 18, no. 12, pp. 285-296, Dec. 2021.
\ [33] Y. Sun, D. Xu, D. W. K. Ng, L. Dai, and R. Schober, “Optimal 3D-trajectory design and resource allocation for solar-powered UAV communication systems,” IEEE Trans. Commun., vol. 67, no. 6, pp. 4281- 4298, Jun. 2019.
\ [34] J. Yao and J. Xu, “Joint 3D maneuver and power adaptation for secure UAV communication with CoMP reception,” IEEE Trans. Wireless Commun., vol. 19, no. 10, pp. 6992-7006, Oct. 2020.
\ [35] E. Tzoreff and A. J. Weiss, “Path design for best emitter location using two mobile sensors,” IEEE Trans. Signal Process., vol. 65, no. 19, pp. 5249-5261, Oct. 2017.
\ [36] H. Xing, L. Liu, and R. Zhang, “Secrecy wireless information and power transfer in fading wiretap channel,” IEEE Trans. Veh. Technol., vol. 65, no. 1, pp. 180-190, Jan. 2016.
\ [37] T. Liu, M. Cui, G. Zhang, Q. Wu, X. Chu, and J. Zhang, “3D trajectory and transmit power optimization for UAV-enabled multi-link relaying systems,” IEEE Trans. Green Commun. Netw., vol. 5, no. 1, pp. 392- 405, Mar. 2021.
\ [38] S. Boyd and L. Vandenberghe, Convex Optimization: Cambridge Univ Press, 2004.
\ [39] A. Filippone, Flight Performance of Fixed and Rotary Wing Aircraft. Amsterdam, The Netherlands: Elsevier, 2006.
\
:::info Authors:
(1) Hongjiang Lei, School of Communications and Information Engineering, Chongqing University of Posts and Telecommunications, Chongqing 400065, China (leihj@cqupt.edu.cn);
(2) Xiaqiu Wu, School of Communications and Information Engineering, Chongqing University of Posts and Telecommunications, Chongqing 400065, China (cquptwxq@163.com);
(3) Ki-Hong Park, CEMSE Division, King Abdullah University of Science and Technology (KAUST), Thuwal 23955-6900, Saudi Arabia (kihong.park@kaust.edu.sa);
(4) Gaofeng Pan, School of Cyberspace Science and Technology, Beijing Institute of Technology, Beijing 100081, China (gaofeng.pan.cn@ieee.org).
:::
:::info This paper is available on arxiv under CC BY 4.0 DEED license.
:::
\
You May Also Like

AguilaTrades' BTC long position size has increased again to over $400 million, with a current floating profit of $3.63 million

Ford Motor Company to Serve as Advisor to Cardano’s Decentralized Cloud Service Lagon
